Yaswant pandey
Wednesday, 26 February 2025
Exploring the Power of Kali Linux Tools
Thursday, 13 February 2025
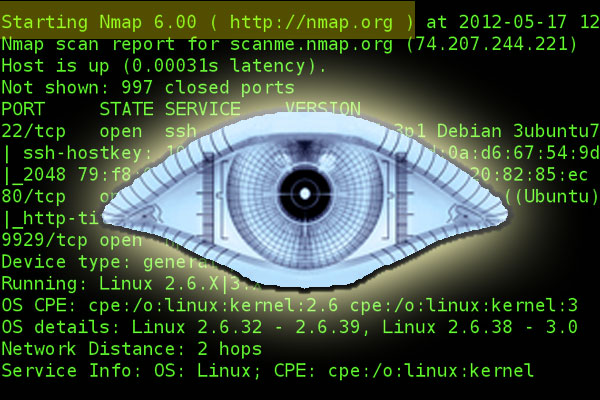
Nmap: The Ultimate Network Scanning Tool
Introduction
Network security is one of the most critical aspects of IT infrastructure. As networks grow in complexity, security professionals need advanced tools to monitor, analyze, and secure them. One such tool that has stood the test of time is Nmap (Network Mapper). It is an open-source network scanner used for network discovery and security auditing. In this blog, we will take a deep dive into Nmap, covering its features, installation, usage, advanced functionalities, and real-world applications.
What is Nmap?
Nmap (Network Mapper) is a powerful command-line tool used for network scanning and host discovery. Originally developed by Gordon Lyon (Fyodor), Nmap is widely used by cybersecurity professionals, system administrators, and ethical hackers for network security assessments. It can rapidly scan large networks to identify live hosts, open ports, running services, and potential vulnerabilities.
Key Features of Nmap:
- Host Discovery - Identifies live hosts on a network.
- Port Scanning - Detects open ports and the services running on them.
- OS Detection - Identifies the operating system of a target machine.
- Service Version Detection - Determines the version of network services running on a system.
- Scriptable Interaction - Uses the Nmap Scripting Engine (NSE) to automate network tasks.
- Firewall Evasion & Bypass - Includes techniques to bypass firewalls and IDS/IPS.
Installing Nmap
Nmap is available for Linux, Windows, and macOS.
Installation on Linux (Ubuntu/Debian):
sudo apt update
sudo apt install nmap
Installation on Windows:
Download the installer from the official Nmap website and follow the setup instructions.
Installation on macOS:
brew install nmap
After installation, verify it by running:
nmap --version
Basic Nmap Commands
1. Scanning a Single Host:
nmap 192.168.1.1
This command checks for open ports on the specified IP.
2. Scanning Multiple Hosts:
nmap 192.168.1.1 192.168.1.2 192.168.1.3
3. Scanning an Entire Subnet:
nmap 192.168.1.0/24
This scans all devices within the 192.168.1.0 subnet.
4. Detecting Host Operating System:
nmap -O 192.168.1.1
This attempts to detect the OS running on the target machine.
5. Service Version Detection:
nmap -sV 192.168.1.1
This provides details about the services running on open ports.
6. Aggressive Scan:
nmap -A 192.168.1.1
This combines OS detection, service version detection, script scanning, and traceroute in one command.
Advanced Nmap Techniques
1. Stealth Scan (Avoiding Detection)
nmap -sS 192.168.1.1
This is a SYN scan that helps avoid detection by IDS/IPS systems.
2. Scanning Specific Ports
nmap -p 22,80,443 192.168.1.1
This scans only ports 22 (SSH), 80 (HTTP), and 443 (HTTPS).
3. Scanning Top 1000 Most Common Ports
nmap --top-ports 1000 192.168.1.1
This is useful when looking for commonly used open ports.
4. Using Nmap Scripting Engine (NSE)
nmap --script=vuln 192.168.1.1
This runs scripts that check for common vulnerabilities.
5. Bypassing Firewalls
nmap -f 192.168.1.1
This fragments packets to bypass some firewalls.
6. Spoofing Source IP
nmap -S 10.10.10.10 192.168.1.1
This tricks the target into thinking the scan is coming from another IP.
Real-World Applications of Nmap
1. Network Discovery
System administrators use Nmap to map out an entire network and understand what devices are connected.
2. Security Auditing
Ethical hackers and penetration testers use Nmap to identify security weaknesses in systems before attackers can exploit them.
3. Compliance Testing
Organizations use Nmap to check for compliance with security standards such as PCI-DSS and HIPAA.
4. Troubleshooting Network Issues
Nmap helps identify open ports, running services, and misconfigured systems.
Graphical User Interface for Nmap: Zenmap
Zenmap is the official GUI for Nmap, making it easier to perform scans without using the command line.
Installing Zenmap:
For Windows, Zenmap is included in the Nmap installation package. On Linux, you can install it using:
sudo apt install zenmap
Conclusion
Nmap is an indispensable tool for network security professionals. Whether you are scanning your own network for vulnerabilities or testing firewall security, Nmap provides a comprehensive suite of functionalities. By mastering Nmap, you can enhance your cybersecurity skills and improve network security within your organization.
Are you using Nmap? Share your experiences and favorite Nmap commands in the comments below!
Tuesday, 3 September 2024
What is server
What is website
Understanding the Basics
A website is a collection of web pages that are linked together and can be accessed via the internet. These web pages are typically hosted on a web server, a powerful computer that stores the files and data necessary for the website to function. When you enter a website's address (or URL) in your browser, you're directing your computer to connect with the web server and retrieve the information stored there.
The Anatomy of a Website
Domain Name: This is the website's address on the internet. For example, "www.example.com" is a domain name. It’s what users type into their browsers to access the website.
Home Page: The first page you see when you visit a website is usually called the home page. It serves as the entry point, giving visitors an overview of what the site offers.
Web Pages: These are the individual pages within a website. Each web page can contain text, images, videos, and links to other pages or websites. For instance, an "About Us" page tells visitors more about the company or individual behind the website.
Hyperlinks: These are clickable elements on a web page that direct you to another web page or website. They are often highlighted in blue and may be underlined.
Navigation Menu: This is a set of links that helps users move around the website. It’s usually found at the top of each web page and may include links to the home page, contact page, blog, etc.
Types of Websites
Websites come in many forms, each serving different purposes. Here are a few common types:
Personal Websites: These are often created by individuals to share personal interests, hobbies, or professional portfolios. They can be simple, like a blog or resume site.
Business Websites: Businesses use websites to promote their products or services, connect with customers, and provide essential information such as contact details and location.
E-commerce Websites: These sites allow users to buy and sell products or services online. Examples include Amazon and eBay.
Educational Websites: These provide educational content, often in the form of courses, tutorials, or research materials. Examples include Khan Academy and Coursera.
Social Media Websites: These platforms enable users to connect, share, and interact with each other. Examples include Facebook, Twitter, and Instagram.
How Do Websites Work?
When you enter a URL into your browser, several things happen in the background:
DNS Lookup: Your browser sends a request to a Domain Name System (DNS) server to find the IP address associated with the domain name you entered. Think of DNS as the internet's phone book.
Server Request: Once the IP address is found, your browser sends a request to the server that hosts the website.
Response from Server: The server processes the request and sends back the files that make up the web page you want to view, usually in HTML, CSS, and JavaScript.
Rendering: Your browser takes these files and renders the web page, displaying it on your screen.
Why Are Websites Important?
Websites are a crucial part of the internet ecosystem. They allow individuals and organizations to reach a global audience, provide information, and offer services online. Whether you're reading the news, learning a new skill, or shopping for your favorite products, websites are the gateway to the digital world.
Conclusion
In essence, a website is a collection of web pages accessible over the internet, serving a wide range of purposes from personal expression to business and education. As the internet continues to evolve, websites remain fundamental to how we access and share information online. Whether you're a casual user or someone looking to create your own site, understanding what a website is and how it works is the first step in navigating the vast online landscape
what is internet
The Internet is a vast global network that connects millions of private, public, academic, business, and government networks worldwide. It enables computers, smartphones, and other devices to communicate with each other, share information, and access services and resources. Here's a detailed explanation of the Internet:
1. Origins and Development
- Origins: The Internet's origins trace back to the 1960s with the creation of ARPANET, a project funded by the U.S. Department of Defense's Advanced Research Projects Agency (ARPA). ARPANET was initially designed to allow multiple computers to communicate on a single network.
- Development: Over time, ARPANET expanded and integrated other networks, eventually becoming the foundation of the modern Internet. By the 1990s, the Internet began to evolve into a commercial and public network accessible to a global audience.
2. Basic Components
- Networks: The Internet is a network of networks. It connects Local Area Networks (LANs), Wide Area Networks (WANs), and other types of networks using various technologies.
- Protocols: Internet communication is governed by protocols, which are standardized rules and procedures. The most important of these protocols are:
- IP (Internet Protocol): This protocol is responsible for addressing and routing data packets so they can travel across networks and reach the correct destination.
- TCP (Transmission Control Protocol): TCP ensures that data sent over the Internet arrives accurately and in the correct order.
- HTTP/HTTPS (Hypertext Transfer Protocol / Secure): These protocols are used for transmitting web pages over the Internet.
- FTP (File Transfer Protocol): FTP is used for transferring files between computers on the Internet.
- Routers and Switches: These devices direct the flow of data on the Internet. Routers determine the best path for data to travel, while switches connect devices within a network.
- Servers and Clients: Servers are powerful computers that provide data, services, or resources to other computers (clients) over the Internet. Clients request information from servers, like web browsers requesting web pages.
3. How the Internet Works
- Data Transmission: When you send data over the Internet, it's broken into small packets. Each packet travels independently across networks and is reassembled at its destination.
- Domain Names and IP Addresses: Each device on the Internet has a unique IP address (e.g., 192.168.1.1) that identifies it. To make navigation easier, domain names (e.g., www.google.com) are used, which are translated into IP addresses by the Domain Name System (DNS).
- Web Browsing: When you type a URL into your browser, the browser sends a request to the server hosting the website. The server responds by sending the web page data back to your browser, which displays it for you.
4. Services Provided by the Internet
- World Wide Web (WWW): The web is a vast collection of interlinked hypertext documents and resources, accessed through web browsers.
- Email: Email allows users to send and receive messages over the Internet.
- Social Media: Platforms like Facebook, Twitter, and Instagram enable users to share content and communicate with others.
- Streaming: Services like YouTube, Netflix, and Spotify allow users to watch videos and listen to music in real-time over the Internet.
- Cloud Computing: The Internet enables remote storage and computing services, allowing users to access files and applications from anywhere.
5. Security and Privacy
- Encryption: To protect data transmitted over the Internet, encryption techniques like SSL/TLS are used, especially for sensitive information such as passwords and credit card numbers.
- Firewalls and Antivirus: These tools protect computers from malicious activities and cyber threats by filtering traffic and detecting harmful software.
- Privacy Concerns: The Internet raises privacy issues, as personal data can be collected, tracked, and potentially misused by various entities.
6. Impact on Society
- Communication: The Internet has revolutionized communication, making it instant and accessible across the globe through emails, instant messaging, and video conferencing.
- Commerce: E-commerce has flourished, enabling businesses to reach customers worldwide and providing consumers with a vast array of products and services at their fingertips.
- Education: Online learning platforms have expanded educational opportunities, offering courses and resources to people anywhere with an Internet connection.
- Social and Cultural Impact: The Internet has influenced social interaction, culture, and entertainment, creating a global community where ideas and trends can spread rapidly.
7. Future of the Internet
- Expansion of Connectivity: Efforts like satellite-based Internet (e.g., Starlink) aim to provide global Internet access, especially in remote areas.
- Internet of Things (IoT): The IoT connects everyday devices (like smart thermostats, refrigerators, and cars) to the Internet, enabling them to communicate and be controlled remotely.
- Cybersecurity Challenges: As the Internet continues to grow, so do the challenges related to cybersecurity, requiring ongoing efforts to protect users and data.
The Internet has become an integral part of modern life, transforming how we work, communicate, and interact with the world around us. Its continuous evolution promises even more profound changes in the future.
Exploring the Power of Kali Linux Tools
Introduction Kali Linux is an advanced penetration testing and security auditing distribution, beloved by cybersecurity professi...

-
The Internet is a vast global network that connects millions of private, public, academic, business, and government networks worldwide. It e...
-
Understanding the Basics A website is a collection of web pages that are linked together and can be accessed via the internet. These web pag...
-
Introduction Network security is one of the most critical aspects of IT infrastructure. As networks grow in complexity, security profession...